Quote:
Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code as cleverly as possible, you are, by definition, not smart enough to debug it.
Don't take security lightly!
My home server was barely up on the Internet for 3 days when I find login attempts as root, test, admin, guest and oracle. These are the most common from a total of 1000+ different names.
None of them will ever succeed for two reasons. Either the accounts don't exist or they are not allowed to SSH in. (I only allow a small number of users to log in from the Intranet and an even smaller number from the Internet.)
I am wondering whether I should move my SSH port from 22 to some other number to reduce the log incidents. However, a simple port scan will reveal the new port just as easily.
It is a very good thing a NAT router also serves as a firewall, or a Windows machine will be rooted very easily.
(Joke: what do you call a Windows machine on the Internet? Answer: a bot.)
I am now convinced we need to enforce the following for a general user (whom you can't trust to have a strong password):
- Create a special SSH a/c for users to SSH in
- The SSH id must not be well-known.
- The password must be sufficiently strong.
- After the user logs in, he
suto his real a/c.
It doesn't work for VNC sessions, though.
How PHP tries to restrict file system access
In an earlier article, I said a poorly written script can expose files outside of the website:
http://<site>/scripts/minify.php?f=/../../../etc/passwd
I found that PHP can stop this using its open_basedir
settings. When this is set, only directories under the specified paths are
allowed.
The script will now fail. Mission accomplished?
Almost. There are three drawbacks:
- PHP also turns off some file/dir caching, so it now parses paths much slower.
- It can be bypassed by a determined local user in PHP.
- It can be bypassed trivally with Unix commands.
Bypassing, the PHP way
The flaw is that the path checking and accessing is not an atomic operation. This gives rise to a race condition vulnerability:
- Script 1 continuously opens a specially prepared symbolic link. It will fail most of the time.
- Script 2 continuously alternates the specially prepared symbolic link between an allowed file and the disallowed target file.
This sequence of event will allow access:
- Script 2 sets the symbolic link to an allowed file
- Script 1 checks that the symbolic link is allowed
- Script 2 sets the symbolic link to a disallowed file
- Script 1 now opens the symbolic link
We have to turn off symbolic link in PHP to avoid this vulnerability.
A special symbolic link can be prepared in 5 steps:
- mkdir("a/a/a");
- symlink("a/a/a", "b");
- symlink("b/../../../", "special");
- unlink("b");
- symlink(".", "b");
So many steps are needed because PHP checks the symlink is a valid and allowed path at each step.
This sort of symlink manipulation has been around for years on multi-user Unix environments, but it is refreshing to see it used on a webserver.
Bypassing, the shell way
This often works:
echo "<pre>" . `ls -l /` . "</pre>";
It completely bypass open_basedir because it is only
enforced by PHP.
This works as well:
echo "<pre>" . `cat /etc/passwd` . "</pre>";
Getting the list of users is always the first step towards finding a user with poor security.
(We need to read the passwd file as /home is usually unreadable.)
We have to turn off shell access in PHP to avoid this vulnerability.
To sum up
open_basedir helps to protect against poorly written
scripts, but it is not a cure-all. Remember, there is no magic bullet.
Watch out for the file permissions!
Ubuntu's default umask setting is 022. In English, this gives read access to everyone.
Being more security conscious, we change the default umask to 077 in /etc/profile. This gives full access to the user only.
Note that the umask setting affects only new files. Existing files must be manually chmod. In other words, this step should be done asap.
For savvy users, we can change the default umask to 027 in ~/.profile. This gives read access to the group as well.
By default, a user is in his own group. However, I find it useful to make all (human) users part of the users group:
useradd -g users <user>
(-g makes it the primary group. -G just adds it as a secondary group.)
This allows files to be shared more easily between users.
Again, this should be done asap. Existing files can be converted using chown.
Why is file permission important?
One word: security breach.
Scenario 1: suppose a hacker is able to breach Apache or PHP. Apache runs as www-data. Can the hacker read other users' files? Not if the permissions are set right. (By default he can.)
If he can't read other users' files, he has to mount a separate privilege escalation attack to gain root access. This is the second line of defense.
Scenario 2: suppose a hacker breaks a user's weak password. Can he read other users' files? Not if the permissions are set right. (By default he can.)
Putting a home server on the Internet
It is pretty easy to put a home-based server on the Internet — although it may violate your ToS (Terms of Service). This is even cheaper than the cheapest webhosting package (S$100 + S$15 for the domain name, per year).
Basic steps
First, we sign up with a DDNS service provider, so that we can locate our
server easily. Instead of typing an arcane 1.2.3.4 that changes
every time we reboot our modem, we just need to type in, say,
mysite.dyndns.org.
(There are no good free domain names. We can register one for ~$15/year, though.)
Second, we configure our modem to automatically register its WAN IP address with the DDNS service provider.
Third, we configure our router to forward the relevant ports to our server. Typical ports are 22 (SSH), 80 (HTTP) and 443 (HTTPS). Note that we do not need to forward port 5901 (VNC) because we will tunnel through SSH instead.
That's it, we are on the Internet!
Security
The Internet is a very hostile place. There is nothing like putting our own server there to make us paranoid about security.
First, we want to restrict who can log in from the Internet. This can be done by configuring /etc/ssh/sshd_config. root should definitely be disallowed.
And instead of VNC'ing directly to the server, we VNC through a SSH tunnel. VNC transfers in "clear", so it is a bad idea to run VNC as-is over the Internet. Again, it is not very difficult to set up.
The next thing that we definitely want is to access our website over HTTPS. This is especially true for admin pages, such as cPanel (Website management) and phpMyAdmin (administers MySQL databases).
The good thing is that it is pretty easy to generate our own self-signed certificate and configure Apache to use it.
Then, we want to configure Apache and PHP to leak as few information as possible by turning off some HTTP response headers.
Passwords
Passwords are still the keys to the server. If a attacker knows a password, he has access to the server, so choose a strong password!
There are 3 main passwords to watch out for:
- Passwords of all users who can log in from the Internet
- VNC password (not so important since need to get past SSH)
- MySQL password (exposed through phpMyAdmin)
A semi-strong password is at least 8 characters, has 1 digit and 1 symbol.
It is too easy to write insecure code
It is very hard to write secure code — because of our tools and programming techniques.
Buffer overrun
In this era and time, we still have fixed-size arrays and strings that don't know their own size.
Fixed-size arrays are easy to overrun for three reasons:
- Array bounds are not checked
- Array bounds are checked only for the debug build
- Array bounds are checked, but not handled properly
Fixed-size arrays is an archaic programming construct. The programmer needs to decide the worst-case size up-front. If it is much higher than the normal case (usually the case), and allocating for it is not feasible, that is when problem arises.
This is made worse by languages that cannot share an array properly, but require different parts of the program to have their own private copy. Each copy introduces a potential buffer overrun bug. And each copy with the worst-case size adds up pretty quickly.
Fixed-size strings are like arrays, but they are even easier to overrun
due to insecure functions: strcpy(), strcat(),
sprintf() and the like.
Now, it is trivial to replace sprintf() with
snprintf(), but it is not so trivial to use
strncpy() and strncat(). For one thing, they do not
store the NUL ('\0') terminator. We need to do it ourselves. This
is even worse than a potential buffer overflow bug because it is a guaranteed
bug.
(Note: it is also not trivial to replace strcmp() with
strncmp().)
I've seen code that introduces this bug because some dumb lint program says
strcpy(), strcat() and strcmp() are bad
and should be avoided.
What happens when the buffer is overrun?
If the variable is on the stack, then the attacker will be able to overwrite other stack elements, including the return address.
So, he injects machine code as the input and overwrites the return address such that it "returns" to the machine code. This requires some trial and error, but once accomplished, it will work every time. (Otherwise the program just crashes.)
This is avoided to a large extent if the OS, together with proper CPU support, disallows program execution from the stack. Modern OS do this.
Even so, hackers have found a way to hack with the so-called return-to-libc attack.
Is the machine compromised?
The executing program is compromised. If it has administrative access, the machine is compromised. This is why it is extremely advisable to run programs as a non-privileged user: when a non-privileged program is compromised, the attacker needs to mount a separate privilege escalation attack to gain administrative access.
Note that a browser or a webserver should be run as a separate user, so that your files — which can be important and sensitive — are not compromised.
(Modern OS have proper user-access controls. However, they are not used most of the time for convenience.)
Is dynamic-sized arrays the answer?
It helps with memory management, but it is still not free from attacks. The attacker can now mount a Denial-of-Service (DoS) attack by causing the array to grow to consume the available memory.
Should strings know their own length?
These strings are more secure, but due to legacy functions or systems, we
will have a mix of the two. Some parts of the program accept NUL,
but some parts do not — and this is a potential for exploitation.
In fact, this was how users were tricked into clicking malicious URLs a few years back. (The display code stops at the first NUL, while the rest of the browser handles the entire string.)
String injection
Many systems use strings to execute commands. The problem starts when we substitute user input without filtering or escaping the special characters — and there are always special characters.
SQL
The most famous of all string injections is the SQL-injection.
snprintf(buf, buf_size, "SELECT * FROM users WHERE name = '%s';", user_name);
What happens when user_name is ' or '1'='1? The
query becomes:
SELECT * FROM users WHERE name = '' or '1'='1';
Voila, we get all the users!
HTML
HTML is susceptible too. HTML injection is also known as Cross Site Scripting.
Suppose we have a blog and we didn't sanitize the user comments before displaying them:
var text = $("#user-input").val();
$("#preview").html(text);
This allows the user to put whatever HTML element they want: typically external links or some rogue external JavaScript files.
Being able to execute an external JavaScript file is a big deal because there are other JavaScript/CSS vulnerabilities that allow the attacker to gain control of the current session or even the user's PC (in the case of a browser vulnerability).
Using user input as keys directly
It is well known we should not trust user input, but it is still not easy to do it correctly.
Filesystem
A classic example is using the user input to retrieve a file directly. There are two potential problems:
- The user may access a file in the website he has no access to.
- The user may access a file outside of the website
(1) works because the webserver (Apache) may call an external program (PHP) which does not know about the webserver's permissions.
For example, if we have a PHP script that minifies JS/CSS files:
http://<site>/scripts/minify.php?f=<file>
Suppose we call it directly:
http://<site>/scripts/minify.php?f=/.htaccess
A poorly written script will return the file. .htaccess is otherwise usually protected by Apache.
All the server-side scripts can be leaked this way if not careful:
http://<site>/scripts/minify.php?f=/scripts/minify.php
(2) looks even more serious:
http://<site>/scripts/minify.php?f=/../../../etc/passwd
Suppose the website is hosted at /home/<user>/public_html, this will get /etc/passwd, or the system's password file! (Well, it gives us the user ids.)
However, the damage is usually not that serious because the webserver runs as a separate user. The user's own private files will not be compromised if he sets his file permissions correctly. (Unfortunately, they are usually not setup that way by default.)
The solution is to sanitize the user input, but it is easier said than done.
(1) is a tradeoff between flexibility and security. Some security is necessary, but we also do not want to lock down the script too much, else we need to update it very often.
(2) is pretty straightforward, but the code can be slow if not designed properly. It can also be buggy if not tested properly.
User-specified keys
Sometimes, when we want to write a generic update function, we allow the webpage to specify both the key and value. (The keys are hidden from the user, of course.)
The problem is that the attacker can specify his own keys and access fields not otherwise exposed by the webpage.
So, how do we write secure code?
Rule 1: there is no magic bullet.
Rule 2: be paranoid.
Programming is not easy.
Park at your own risk
News: TP to stop booking vehicles for illegal parking from Nov 1
Soon, you will no longer see a Traffic Police (TP) officer booking vehicles for illegal parking offences.
From Nov 1, the Land Transport Authority (LTA) will be taking over five functions from the TP the duty of enforcement against illegal parking offences.
The government statutory board will be empowered to close roads or lane for repair, alongside issuing permits for vehicle loads and the use of excluded vehicles such as mixers, on expressways.
LTA will also be gazetting speed limits on roads.
The functions above were identified as in line with LTA's role to manage road usage, said Mr Colin Lin, LTA's acting group director for vehicle and transit licensing.
The Commander of Traffic Police, Assistant Commissioner of Police, Cheang Keng Keong, said the transfer of duties will allow them to better focus on their core functions such as enforcement against unsafe driving behaviour.
Upon taking over the enforcement of illegal parking, LTA will deploy traffic wardens, auxiliary police officers and its own uniformed enforcement officers to carry out the function.
LTA's enforcement procedures will be similar to those of the TP.
There will be no change to the penalties for illegal parking offences.
Members of the public can call LTA's hotline 1800-CALL LTA (2255 582) on illegal parking matters from Nov 1.
TP will continue their enforcement action against speeding offences.
Issuing permits for carrying of loads on vehicles
LTA will take over the issuing of permits for oversized vehicles to travel on the roads.
Vehicle owners or drivers can make use of LTA's on-line portal, LTA.PROMPT, to submit their applications.
The details of the application process will be made available to the relevant stakeholders closer to the date of takeover.
More details on any changes in procedures affecting members of the public will be available on www.onemotoring.com.sg and https://prompt.lta.gov.sg nearer to 1 November 2010.
Members of the public may also call the LTA hotline at 1800-CALL LTA (2255 582) for more information.
Currently, it is pretty safe to risk parking on pavements, double-yellow lines and other illegal spots under TP's jurisdiction, even though the fine is a hefty $70. The reason is that TP is seldom in action.
($70 may not seem much, but you can park legally for over 100 days!)
No more. It is now better to park legally. LTA has many more enforcement officers than TP.
A true sense of perspective
News: In one day, two asteroids buzz the Earth
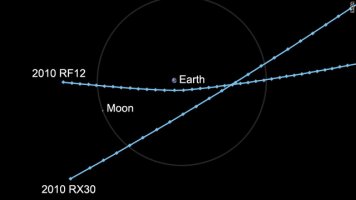
Two small asteroids passed within the moon's distance from the Earth about 12 hours apart on Wednesday, NASA confirmed.
Near-Earth asteroid 2010 RX30, which is estimated to be 32 to 65 feet in diameter, passed within 154,000 miles of Earth around 5:51 a.m. ET Wednesday. The second object, 2010 RF12, estimated to be 20 to 46 feet in diameter, passed within 49,088 miles of Earth close to 5:12 pm ET.
That means the two asteroids passed within 0.6 and 0.2 lunar distances from the Earth, respectively.
The group is awaiting official data from observatories across the world to confirm the exact time, sizes and orbits of the two objects, said Donald Yeomans, manager of NASA's Near Earth Program, which tracks potentially hazardous asteroids and comets within 28 million miles of Earth.
Wednesday's double encounter was unusual in the sense that NASA spotted the objects three days in advance and successfully plotted their orbits, he said, demonstrating the need for closer monitoring of near space for Earth-threatening encounters.
"It just confirms that the process we have in place — whereby we observe and find them and then we quickly predict when they'll pass Earth and get that info out — that process works pretty well," Yeomans said. "The search for the next one goes on."
The objects did not threaten Earth, and could only be seen as tiny specks of light using moderately sized amateur telescopes. Stony objects of the two asteroids' size would not be expected to make it through the Earth's atmosphere, but would put on "a great light show," Yeomans said.
Roughly 50 million objects pass through near-Earth space each day, Yeomans said. The more information NASA has on those objects in advance, the more it can do to prevent potential threats to Earth, he said.
"Things like this happen every day that we simply don't know about because we don't have the telescopes large enough to find them or surveys that are looking full-time," he said Tuesday.
Technology exists to adjust an object's path by directing an explosive device at it or running into it, just as the Deep Impact Spacecraft ran into the Comet Temple on July 4, 2005, he said.
"If you have several years warning, you can do it just by nudging it several millimters to change its path just enough to miss the earth," he said.
The Catalina Sky Survey near Tucson, Arizona, discovered both objects Sunday morning during a routine monitoring of the skies, NASA said. The Minor Planet Center in Cambridge, Massachusetts, first received the observations Sunday morning, determined preliminary orbits and concluded both objects would pass within the distance of the moon about three days later.
Yeomans described the discovery as a warning shot in a field of study of low-probability events with global, high-impact consequences.
"We have only recently appreciated how many of these objects are in near Earth's space," he said. "I think this is Mother Nature's way of firing a shot over the bow and warning Earth-based astronomers that we have a lot of work to do."
Mere pebbles, in the grand scheme. We won't even feel it if they hit us. In contrast, the famous asteroid from 65 million years ago that paved the way for mammals was estimated to be 10 km wide.
It frustrates me sometimes that we are in the age of science and technology and yet we are not making use of them properly — we should try to get off this rock!
Think COE is high? Wait for this
News: Move to have zero vehicular growth to tackle road jams "imminent"
Congestion on Singapore's roads has renewed calls for more aggressive measures to curb the vehicle population.
One solution is to have zero vehicular growth, a point raised by Senior Minister Goh Chok Tong at a dialogue with grassroots leaders recently.
Observers said implementing such a move is imminent as Singapore roads are nearing maximum capacity.
Singapore's vehicle population has grown to about one million. With limited land, vehicle growth rate has been set at 1.5% for the next two years.
But, is this sustainable?
Dr Lim Wee Kiak, chairman of Government Parliamentary Committee for Transport, said: "We should maintain our current fleet of vehicles, not to increase further. Perhaps, given a chance, Ministry of Transport should consider a reduction in vehicle number rather than (an) increase.
"We are looking at a reduction in growth, but what I will like to see is to reach the zero (growth) faster. In Parliament, we have been pushing for some sort of a zero growth, if not, even a negative growth to counteract the excess over the last few years.
"They should release (fewer) COEs compared to the number of vehicles taken off the roads so that there is actually a reduction in the number of vehicles in Singapore."
The reduction in COEs will mean higher car prices. Is this likely to get more people on public transport?
"I will still strive to get a car, even if the price is high," said a member of the public.
"I still want to own a car," said another.
"If you are holding a certain position, you may need it (car) for the image," said a third.
"I will give up my car, if the transport in Singapore is able to achieve the coverage.....(such that) we can go anywhere conveniently," said a fourth.
Such reasons are why many say aggressive measures are needed to convince people to take public transport.
One suggestion has been for public transport operators to offer fare discounts for travel during off-peak hours, as this is likely to tackle the problem of overcrowding in trains.
Dr Lim Wee Kiak said that with discounts, more people would consider spreading out their travel. "So there would be spaces for everyone," he said.
Buses must also become a more reliable alternative, said Associate Professor Lee Der Horng from the Department of Civil Engineering at the National University of Singapore (NUS).
He said: "We must take some very aggressive approach. What we have to do is, other than the MRT, we have to pay more attention to the buses.
"Can we provide more full-day bus lanes? Can we give higher priority to public transportation vehicle like the bus? Can we improve the level of bus service, have cleaner buses, newer buses, faster buses, safer and more comfortable (bus travel)?"
Meanwhile, the Land Transport Authority (LTA) said it will conduct a review in 2012 to determine an allowable vehicular growth rate. It also said that even if the growth rate is reduced to zero, there will still be a need for usage measures to effectively manage demand for roads.
Never let go once you buy a car. You may not be able to afford the COE again.
Existing car owners can always choose to keep their cars, while aspiring car owners will bid the even-more-limited COE supply sky high.
Singapore's policies have a way of backfiring because they never consider the unintended consequences.
Calling for more local gamblers
News: Free IR bus rides probe
THE Government is investigating the free bus rides offered by the two integrated resorts (IRs) here.
The probe could have an impact especially on Resorts World Sentosa (RWS), which introduced free shuttle services between the resort and 12 HDB town centres a few months ago.
The investigation, announced yesterday by the Ministry of Community Development, Youth and Sports (MCYS), is to establish that Singaporeans are not being encouraged to go to the IRs' casinos.
It comes amid protests from MPs like Mr Liang Eng Hwa (Holland-Bukit Timah GRC), who told The Straits Times earlier that the free rides encourage Singaporeans in the heartlands to gamble at the casinos. He will raise the issue in Parliament.
When contacted about Mr Liang's concerns, the ministry said in an e-mail reply: 'We are investigating the provision of free transport by the IR operators.
'The IR operators will not be allowed to target the local market or provide incentives in any form for Singaporeans to patronise the casinos.'
Its move is in line with legislation introduced in 2006 to regulate casinos. The law, among other things, forbids casino advertisements in the mass media.
The National Council on Problem Gambling also views the free shuttle services with 'great concern'. Its statement said it 'disapproves of any marketing and promotion effort targeting Singaporeans and permanent residents to visit the casinos.
'We will work closely with MCYS to address any possible social impact arising from casino gambling.'
Both IRs offer free shuttle services. The Marina Bay Sands shuttle goes between the resort and Changi Airport, as well as hotels in the Marina Bay area. The RWS buses are available at two spots in the Central Business District - International Plaza and Lau Pa Sat - as well as at 12 HDB town centres, including Ang Mo Kio, Jurong East, Tampines and Bedok.
Most of its bus services run from 10am to 10pm on weekdays. On weekends, the last bus leaves for RWS at 2.20am.
Yesterday, The Straits Times went on 17 trips between 10am and 9pm, taking buses between RWS and HDB town centres in Choa Chu Kang, Tiong Bahru, Bedok and Bukit Merah. Most buses were 50-seaters.
On the day trips, one in seven commuters walked straight into the casino upon getting off the bus. At night, after the Universal Studios theme park closed at 7pm, two out of five headed for the casino, which Singaporeans have to pay $100 to enter.
Most of the 30 commuters interviewed said they came to know of the free shuttle after receiving RWS mailers in their letter boxes.
Among them was a 60-year-old retiree who took the 10am bus from Choa Chu Kang. He was bringing his family of six, including two grandchildren, to the Universal Studios theme park.
'We're going because it's my grandson's birthday. I've never been inside the casino. The $100 fee is too expensive,' he said.
Teenagers and families with children formed the majority on the buses during the day, and were usually headed for Universal Studios or the food outlets. On the night services, the buses were half-full, mainly with workers.
Clerk Jeanette Chan, 45, who visits the RWS casino six times a month, said: 'The buses make it really convenient as it stops at an indoor bus bay not far from the casino.'
Previously, she had to cross a road to get public transport home. 'And when it rained, I got wet,' she added.
RWS, however, said a survey it did of 2,500 users of its free shuttle shows more than 60 per cent did not go to the casino. It also said that 'we do not provide special casino incentives to Singaporeans'.
Six MPs interviewed whose wards are served by the free shuttle say the concerns over gambling are valid. However, they feel people should keep an open mind as the free bus services benefit those who want to visit the other attractions on Sentosa.
Said Mr Baey Yam Keng (Tanjong Pagar GRC): 'I don't think it's a big deal... if people want to go, they can easily make their way to the casinos.'
Like some of the other MPs interviewed, Mr Baey said none of his constituents had approached him about problem gamblers in their families.
Mr Seah Kian Peng, chairman of the Government Parliamentary Committee for Community Development, Youth and Sports, said the shuttle to Sentosa should stop at 7pm when Universal Studios closes.
He added: 'If the aim of RWS is to draw more to patronise the casino, then that is wrong.'
When the IRs were being built, the Government said local jobs and foreign gamblers. It turned out to be local gamblers and foreign jobs.
Things do not always go the way you plan, especially if you plan for the best case only.
One thing not addressed here is that it does not seem very difficult/expensive to provide free island-wide shuttle service. It makes you wonder why the bus/MRT fares are going up year after year.
News: WHAT CASINO? IT'S A FREE RIDE
'I'm not going to the casino. Actually, I'm not even going to Sentosa. I'm planning to spend the day in Tampines Mall. So I'm taking the free bus from home in Choa Chu Kang to Sentosa. I'll then hop on the next bus from Sentosa to Tampines. It's my way of beating rising bus fares.'
A 48-year-old unemployed Choa Chu Kang resident who declined to be named
Ding ding ding, we have a winner!
Be a citizen, or go home
News: SM Goh: surge of immigrants caught govt by surprise
Take rational approach to problems: SM Goh. See pressing issues like housing, transport in perspective, he urges
WHEN Senior Minister Goh Chok Tong was a young civil servant working in the former Fullerton Building, he had, on occasion, waited as long as one hour to catch a bus home. Today, most people who fail to get on a packed MRT train have to wait just six to eight minutes to get on the second or third train.
But that is a long wait for them, he noted yesterday, when he drew the comparison to emphasise that Singapore can solve its most pressing problems as long as people adopt a rational approach towards them.
He made the point at a dialogue with 200 grassroots leaders at the Marine Parade Community Club, held to gather feedback on the issues Prime Minister Lee Hsien Loong covered in his National Day Rally speech a week ago. Beyond transport, he also discussed the hot issues of housing, education and immigration, making the point that these are complex subjects and that every solution has its consequences.
To illustrate, he cited the new signalling system for easing MRT congestion by cutting waiting times for trains. 'You may have to spend about $1 billion just to change the system. What is unsaid is: Who is going to pay for this? 'If we tell you that fares are going to go up, there will be a huge howl of protest...But sooner or later, the cost must be defrayed,' he said. Reiterating the message he made over the weekend, he said these challenges were the result of Singapore's success and ought to be viewed in perspective.
Mr Goh, flanked by MPs Ong Seh Hong and Lim Biow Chuan, then asked the grassroots leaders from their three respective wards - Marine Parade, Kampung Ubi-Kembangan and Mountbatten - to suggest solutions that the Government could consider. It prompted a former national serviceman to urge the Government to consider giving those who have completed their service some form of recognition.
This is because they do not benefit from the latest NS Recognition Award, which gives NSmen up to $9,000 and commanders up to $10,500, which they can use to help pay for HDB homes. Mr Goh assured him that the sacrifices made by the older generation were no different, but noted they would have benefited in other ways, like having bought their HDB flats at a 'cheaper' price.
Still, the Government will take note of the suggestion that something could be done for former NSmen, he added. Mr Lim, however, said he was uncomfortable with the award as many people feel loyalty has no price - a remark that drew loud applause.
On housing, Mr Goh acknowledged that the surge of immigrants in 2007 and 2008 caught the Government by surprise. But the Government had not stopped them from coming because the booming economy needed workers.
Mr Goh also acknowledged the National Development Ministry 'did not provide for the sudden surge' in its housing plans. He then asked the audience for a show of hands on how they would rank, in order of importance, these issues: the economy, education and immigration. A dozen hands shot up for immigration, two dozen for education, and around 100 for the economy.
'That's the right order,' said Mr Goh.
He hinted at a possible change of policy on permanent residents (PRs): 'Moving forward, we are going to approach some to take up citizenship. If they don't, then their PR will not be renewed. That's a better way.'
With about 500,000 PRs, Mr Goh hopes that 'maybe 50,000 can be selected to be citizens and the rest can be PRs, contributing to Singapore's economy.'
Heads I win, tails you lose. That is how the Singapore government deals with its citizens. (Chinese saying: the word 'government' has two mouths.)
I wonder how the government will pick the 10% "lottery" winners...
Prime targets:
- 2 PRs who have bought a HDB flat
- PRs who studied here
- PRs who have stayed a long time here (15 years)
Is remote scanning a security vulnerability?
Most AiO (All-in-One) printers have a "WebScan" feature: it allows the user to scan using the Web-based interface; no installation required.
Most business-class printers, however, require an admin password to use this feature because of security risks.
Security risk: someone can rescan documents left behind. Question: is this a real security risk?
Anyway, let's fix this by requiring admin password.
What's the problem?
Now, normal users who want to use this feature will have the admin password, which then allows them to access much more things. Thus, most users won't get to use this feature at all.
A better solution is to have two passwords: a user password and an admin password.
Another possible solution: if there is a scan lid sensor, we can disable remote scanning until it is opened/closed. (This assumes the user opens it to remove the document.)
A case of double standards
News: To be or not to be a virgin?
For most young people these days, it is no longer an issue but many still believe in having sex only after marriage.
WHAT people do behind closed doors is none of anyone's business.
So says Jo Tey who believes the younger generation today should not be judged on whether they are virgins or otherwise.
For Esther Soh, however, virginity means honouring a promise to God as well as a gift only her husband will receive.
Teh and Soh, both 22 and fresh graduates, are among 50 urban youths aged between 18 and 30 who were interviewed on whether virginity is an issue among young Malaysians today. About 70 per cent responded that it should not be one.
Henry (not his real name) respects people who believe in virginity but claims it will not be a criteria in his seeing someone. He confesses that in his circle of friends, being a virgin is something "despised".
The 30-year-old businessman feels virginity has lost its relevance as it is no longer a criteria in getting into a relationship or a marriage.
Lee Xin Ying, 22, an intern at a government hospital in KL, concurs, saying people today should not expect their partners to be virgins.
But she is strongly against double standards in a relationship where "some guy may have sex with multiple partners but expects his future wife to be a virgin".
Lynn, 25, argues that virginity is still relevant because Malaysian youths are still not well-informed on sex and thus not ready for the responsibilities that come with it.
She, however, does not agree with the perception that a non-virgin, especially a female, is "bad" or "damaged goods".
"Whether a person is forced into sex, made a wrong decision or is ready to take the relationship a step further, there is no reason to stigmatise someone," she says, adding that religion is another main reason why virginity remains a relevant issue.
Mandy, 22, thinks premarital sex is avoidable although she admits it is not easy holding on to values which go against the popular trend.
"It always comes back to what these values mean to me," she says.
Mandy, 22, thinks premarital sex is avoidable although she admits it is not easy holding on to values which go against the popular trend.
"It always comes back to what these values mean to me," she says.
Consultant psychologist Valerie Jacques notes that the importance of virginity is declining due to poor family values.
"Children's basic needs are not being met by money-minded parents. As such, they are drawn to people who use words such as 'I love you' or 'If you love me, then you will give yourself to me' tactics.
"This is a sign of poor self-esteem and confidence, poor self-image and identity. A person with positive esteem, confidence, image and identity will make good choices that bring benefit to themselves and not cause harm. The issue of virginity is then considered in terms of what will bring benefit to the individual who can lose it."
Focus on the Family (FOF) director Ho Kien Keong concurs.
"Most youngsters nowadays think love means sex. Love is a choice," he asserts.
He is concerned that many youngsters see sex as a physical act; one that is as common as eating.
"The physical act stops half an hour later, but consequences last forever," he warns.
In FOF's "No Apologies" pro-abstinence workshops, he adds, teenagers are made aware of the consequences of their actions.
Out of 13,588 secondary school students who attended the "No Apologies" workshops and participated in the FOF survey between 2003 and 2009, 35 per cent found sex before marriage acceptable, citing curiosity and experience as main reasons for the answer.
After attending the workshop, 92 per cent believed sex after marriage is the best choice and signed pledges of abstinence. The respondents are from both rural and urban schools.
Some societies/cultures are obsessed with virginity — but only for the female. No one ever cares if the guy is a virgin or not. That tells us something about the society/culture.
Rather than asking someone whether virginity is important or not, we should ask him at what age does he think people lose their virginity.